

What absolute bull. 🤦


What absolute bull. 🤦


fixed again. jeebus.


Updated with a new link from EBU.
Fair point, edited.
I am still hoping beyond hope they do revive it, there seems to be others that do as well.
Will we get tabbed/grouped windows finally again? Been waiting for this for half more than a decade.


Oh no! The browser that forked the browser that a browser made by the largest ad vendor in the world is based on in order to be able to serve different ads is legally threatening a browser that forked it in order to remove said ads?
Did I get this right?


Actually, if we’re nit-picking, it means “Personal Computer”, but the colloquial meaning has shifted somewhat since the good old IBM times to first mean desktop computers (as opposed to laptops), and then to mean non-Apple computers (including laptops), which for most people means “a computer that runs Windows.”
Which is the basis of my heavy sigh.
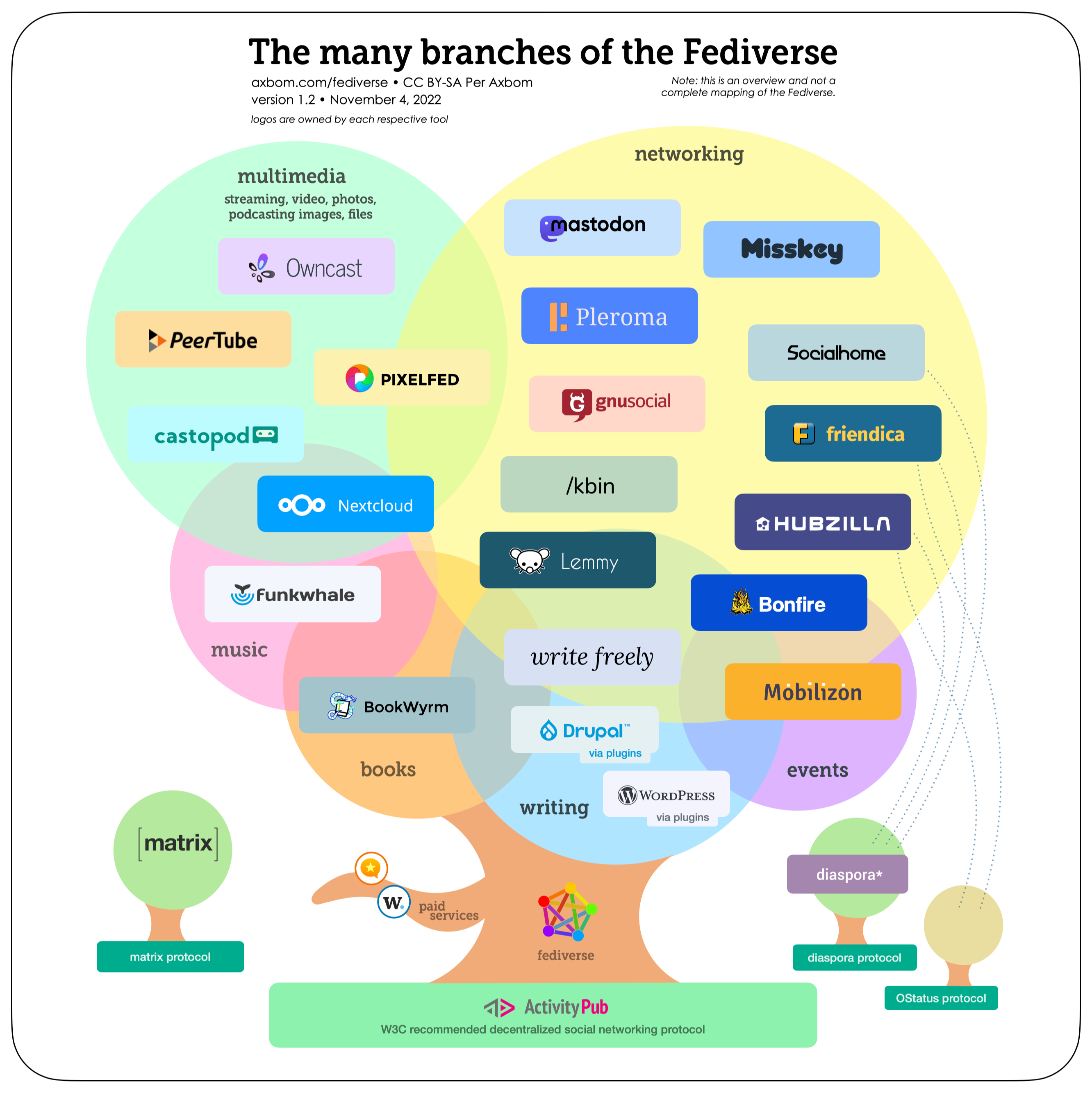
These are just two different software projects that a Threadiverse instance can use. They federate with one another, so it doesn’t matter all that much if you have an account on a Kbin instance, or a Lemmy instance. The differences are in the interface, some functionality, and the tech stack used (Lemmy is written in Rust; Kbin in PHP).
There are 100+ instances of Lemmy, and ~10 instances of Kbin. Kbin is a much younger project (hence it might get missed), and it’s main instance, kbin.social seems to be experiencing more issues with the wave of new registrations. If you want to try Kbin, https://fedia.io/ might be a good instance to check out.


I don’t think you need to worry about it. It’s up to a given community whether or not that baggage affects it or not, I think. Building communities that are very explicitly not tankie is a great way of helping overcome that baggage for the whole project.


Ok, I should have been more specific: the way it is often framed (and the way I have seen it framed, and how the linked article frames it) is as if these were US-affiliated labs working on bioweapons. That is not what Nuland said. Biological research facilities do not have to be bioweapons labs, just as explosives research facilities need not be arms manufacturers.
Greenwald (the author of the linked article) of course does what Greenwald recently is hell-bent on doing, which is to try to scandalize anything he can. I used to respect the man, but that was a long while ago.


This will help:
The source is well-worth visiting and taking the time to read, plenty of additional info!
Well duh. “PC” means “Windows”, obviously.
sigh


I don’t think this phrase means what you think it means; I do in fact put my money where my mouth is.
My mouth is clearly in the “blockchain-based privacy projects are very likely to be either misguided or outright scams, and this particular project has red flags all over” area. And so my money is on “I need to use tools that actually work; there is low likelihood that this project is such a tool; therefore I shall not waste my time on it”.
Demanding that I spent hours analyzing a project that has so many red flags just because you happen do disagree with me is somewhat weird. I’ve spent enough time having this conversation at all, but hey, that’s good entertainment value!
It’s not on me to disprove random project’s exorbitant claims (“prevents traffic analysis by an adversary capable of watching the entire network, including the NSA”). It’s on the project in question to prove them.
So far I have not seen such proof. I have, on the other hand, seen quite a lot of things that suggest that these claims might, in fact, be unsubstantiated.
I could retort by saying: prove to me that the project’s claims are true, “instead of going hurr durr it’s great I love it” (nice veiled ad hominem there, by the way). But I won’t, even though so far I have arguably provided more concrete reasons why I see this project as problematic than you did for your positive take on it.
Telling persons why they’ve decided to use tokens and not rely on pure altruism is not token hyping.
When the rubber hits the road, “using tokens” in this case means simply relying on greed. And relying on greed instead of altruism for something as fundamental as privacy is very telling. It’s not going to end well.


All the claims against tor and i2p are discussed in numerous academic papers and are acknowledged by the developers themselves
I was not talking about claims about i2p or Tor. I was talking about the claims Nym people make about their own project. I see little reason to trust them on those claims.
You’re entitled to your opinion. I am entitled to mine. I don’t think we will see eye to eye here. In 10 years we will perhaps know; I expect Tor to still be around and useful then, as opposed to Nym.


Sure, here’s my comment:
They make extremely strong claims, and strong claims require strong proof. I do not see such proof anywhere. What I see is that they play fast and loose with website visitor privacy and seem to focus mainly on token hyping.
I would not trust it for anything even remotely sensitive. And I still fully expect them to show up on https://web3isgoinggreat.com/ sooner or later.


While security by obscurity may have been cutting-edge at the turn of the millennium, such an approach is rapidly showing its age. Nym’s cutting-edge mixnet design
I think they really need to use “cutting-edge” more in their materials. Will make them look even more serious and trustworthy.
Also, when you quote whole blocks of text from their materials, please have the decency to mark them as quotes.
Anyway, I stand by my assessment.


I’ve read through dozens of white-papers of “revolutionary” blockchain-based tech startups, all promising to solve Very Important Problems, none actually solving such problems. But sure, let’s start here:
Nym tokens provide credentialed access to privacy-enhanced and uncensored internet communication for a unit of time.
This is “privacy for the rich” model. Unsurprisingly: poor people can’t push the token to the moon! And looking at their website it is clear they focus more on hyping the token than on actual privacy.
Speaking of their website, this privacy-focused project done clearly by people that care a lot about digital human rights and want to fight surveillance capitalism directly includes on their website stuff from fonts.google.com, googleapis.com, youtube.com, play.google.com, doubleclick.net. Looks legit to me!
It’s fascinating how they talk down Tor (“because Tor does not add timing obfuscation or cover traffic to obscure the traffic patterns in circuits”), but fail to mention i2p which solves these issues without the need for bollockschain tokens. Makes sense — Nym seems to basically be i2p with a blockchain token bolted onto it so that it can become an investment vehicle.
So either they did not know about i2p, an important and reasonably well known project which has been around for almost 20 years and is very clearly in the same problem space, or they intentionally decided not to mention it because it would make them look bad. Take your pick: are they ignorant, or disingenuous? Either is a great trait for a project that aims at protecting privacy from the NSA, no less.
On a general level, it is safe to assume any blockchain-based project that offers any kind of token and is in any way monetizable is (at best) a solution in search of a problem, or (at worst) a scam, often Ponzi-shaped, until clearly proven otherwise.
I mean, even the most basic promise of Ethereum smart contracts — that smart contracts are binding, transactions are not going to be reverted, and nobody controls the whole network — flew right out the window just because DAO smart contract had a bug and somebody exploited it; and we can’t have that, can we, if people are meant to invest in this, eh?
Privacy and decentralization are too important subjects to be used by cryptobros in their money extraction schemes.
If you think my opinion was not well informed, think again.


Can’t wait until it inevitably ends up on https://web3isgoinggreat.com/ 👀
HAproxy cannot serve static files directly. You need a webserver behind it for that.
Apache is slow.
Nginx is both a capable, fast reverse-proxy, and a capable, fast webserver. It can do everything HAproxy does, and what Apache does, and more.
I am not saying it is absolutely best for every use-case, but this flexibility is a large part of why I use it in my infra (nad have been using it for a decade).