Edit: Solution
Yeah, thanks to u/postnataldrip@lemmy.world I contacted my ISP and found out that in fact they were blocking my port forwarding capabilities. I gave them a call and I had to pay for a public IP address plan and now it’s just a matter of testing again. Thank you very much to everyone involved. I love you. It was Megacable by the way. If anyone from my country ever encounters the same problem I hope this post is useful to you.
Here’s the original post:
Hey!
Ok, so I’m trying to figure this internet thing out. I may be stupid, but I want to learn.
So, what I’m essentially doing is trying to host my own raw html website on my own hardware and get it out to the internet for everyone to see (temporarily of course, I don’t want to get in trouble with hackers and bots) I just want to cross that out of my bucket list.
What I’ve done so far:
- I set up a qemu/kvm virtual machine with debian as my server
- I configured a bridge so that it’s available to my local network
- I got my raw html document
- I’m serving it locally with nginx
- I tried to set up port forwarding (I get stuck here)
Right now everyone in my home can see my ugly website if they go to 192.168.1.114:8080 (since I’m serving it through port 8080).
However, I want to be able to go outside (I’m testing it with my mobile network using mobile data) to see my website.
I’ve configured port forwarding on my ZTE router (ISP-issued) with the following parameters:
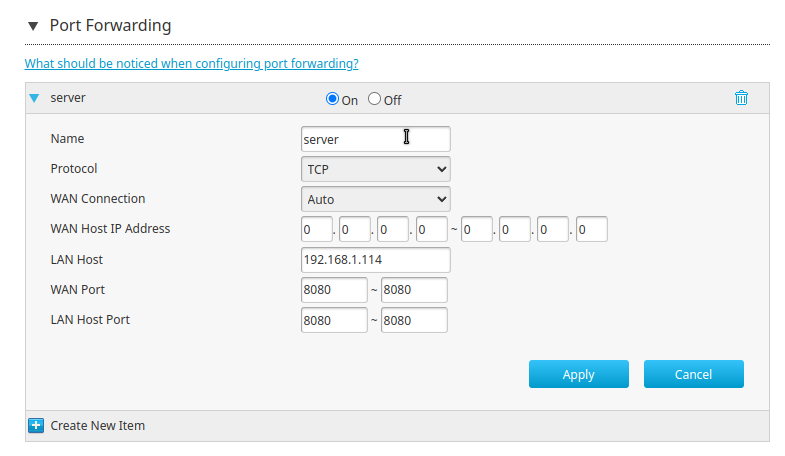
But now, if I search for my public IP address on my phone I don’t get anything. Even if I go to my.public.ip.address:8080 (did you think I was gon-give you my public ip?)
I don’t get anything. I’ve tried ping and curl. ping doesn´t even transmit the packages, curl says “Could not connect to server”.
So, If you guys would be so kind as to point me in the right direction, I pose the following questions :
- How do I even diagnose this?
- What am I missing?
- Am I being too stupid?
- What do I do now?
(Here’s a preview of my ugly website)
I also own a domain (with cloudflare) so, next step is getting that set-up with a DNS or something.
Thank youuuuuuu <3
Does your ISP block ports? Many do, at least where I am. Some allow you to opt-out.
It was, in fact, the ISP
Thank you soooo much!
Are just the specific http/SSH ports blocked?
No, it was a cgnat or something like that.
CGNAT blows, and it’s the reason I pay for a VPS. They have an option to get a static, public facing IP, but it’s more expensive than my VPS, so screw 'em.
How can I check?
Try going to http://000.000.000.000:8080/ in your web browser (replacing the 0’s with your public IP address), on your home connection. If it doesn’t work, it means that your port forwarding is probably not working. If the page loads correctly, it means your port forwarding is working correctly, and the problem is probably your ISP doing port blocking.
I’m trying it just now, the website is not loading. It keeps buffering but nothing happens, it eventually just times out
deleted by creator
That is brilliant, should I be worried? 🤣 (Just noticed I had a message, oops)
I may be stupid, but I want to learn.
Wanting to learn is the least stupid thing there is.
I just hope I don’t put myself at too much risk by doing this. I haven’t got a guide, a mentor or anything, I’m just by myself following random and disconnected youtube tutorials and articles from the web.
I have the same problem, I think the ISP blocks incoming traffic to residential IPs (non static).
You’re probably behind a CGNAT, check out the other comments
Glad you got it working, but you could have hosted it with a tor hidden service and not had to pay for a public IP address and shit.
Cool! How do I go about setting this up? Right now I’m just looking for an equivalent to “launching my first satellite”. It might not be the most secure, and I may be paying more than I should, but I need the motivation, to know that I can and that I did. In the future I’ll be looking for a more sustainable and permanent solution, so I’d appreciate if you could share your arcane knowledge on this “tor hidden service”.
You add the tor repo, install tor, edit /etc/tor/torrc with hidden service info, set the port as 8080 and systemctl restart tor. Then you get a hidden service address in like /var/lib/tor/hiddenservicename/hostname. It’s a long string ending with dot onion and once you have that you just put that into the tor browser.
And with that I’ll be able to see my website anywhere I go? And it’ll technically “be in the darknet”? (or whatever it’s called)
Sounds tempting, is it secure?
Correct, it will be in the dark net. And it’s as secure as your web server. So I guess if your web server is set up in a very insecure manner, it would be very insecure as well. But since nobody would know the onion address besides you or anybody you give it to, it should be all right.
Cool! security by obscurity! I might try it, just to get my website out there, but I don’t see it as a permanent solution
I mean, it’s obviously the only solution, right? You don’t have to pay for a domain name. You don’t have to pay for a hosted IP address. You don’t have to forward ports. You don’t have to do any of that shit. Plus, you’re on the darknet, and everything should be on the darknet. All the time.
Your ISP might make you go through another layer of NAT. Can you find the WAN IP address of your router and compare it to your public IP address from a website such as ipinfo.io ?
If they do not match, you’re probably out of luck and will need to forward your port from an actually public IP in order to achieve what you want
More details : CGNAT (Carrier Grade Network Address Translation) is basically a second router between your router and the public internet. This second router is configured in the same way as your personal one, the main difference being that your ISP fully manages it. From the viewpoint of this second router, your WAN IP is a private IP, and you share one actual public IP with several other customers (the same way all devices on you LAN share one single WAN IP)
Performing port forwarding from the public internet to your LAN, when behind a CGNAT, would require you to be able to configure a forwarding rule in the ISP’s NAT, which you usually cannot do.
Yess!!! Thank you so much! I gave them a call and got the “public ip service” for some extra 5 dollars (in my country’s currency)
Glad I could help :)
Because you’re serving the website on a non-standard port, you will always need to provide the port in the web browser.
That said, I don’t see anything wrong here. It looks like you’ve got the right ports set, TCP should be correct. You may not get a ping, because ICMP is likely not enabled at the modem. When you ping, you ping the first device that’s exposed to the internet, not an open server.
Just to be sure, when you’re on your phone, you’re using data? If you’re on wi-fi, the modem/router may not be configured to perform NAT reflection, so you won’t be able to access anything via your WAN IP.
Yes, I’m using mobile data. I can even check my public ip and it’s different.
Actually, just to double check I connected to my neighbour’s wifi (with his permission) and I’m still not getting the website. I changed the port through which I’m serving the site to port 80 (per another comment’s recommendation) and still not getting anything.
Are you on carrier grade NAT (CGNAT) WAN ip in the address space 100.64.0.0 to 100.127.255.255?
2 potentials
ISP blocking Web hosting ports/traffic - often opt Out or flat out blocked for residential connections.
ISP using CGNAT so your “public ip” isn’t really public? But you got this far so i would guess you already know that.
For reference, the cgnat “public ip range” should be 100.64.0.0 to 100.127.255.255
If you do have cgnat i think maybe cloudflare tunnels, tailscale or a vps are your solutions.
Yes, it was the ISP, I gave them a call and now I have a public ip address.
I, however, would like to learn more about cloudflare tunnels, tailscale, and vps for security reasons. Once I set my first foot on the internet, I would like to find a more permanent solution so that my ugly website may be suffered by many.
If you have any resources on VPNs (I’m considering wireguard) or Cloudflare tunnels, I’d appreciate it.
I was in your shoes a few years ago, so I think I can give at least some insights: Regarding VPNs, Tailscale is based on Wireguard, but makes configuration a whole lot easier, especially if you have devices with changing addresses. You do still need an account with them, but from there you simply install tailscale on every device you want to access via your VPN, and they should automatically get assigned IP addresses (100.x.x.x). Entering this assigned IP from any other device connected to your Tailscale network will give you a direct connection between the two. With a bit of fiddling you can also enable subnet forwarding, allowing you to for example connect to devices on your home network that don’t support installing software on them, but at least for your current setup I don’t think that’s necessary. It is fun to play around with though, and opens up a whole new world of possibilities. I use it to remotely manage my parent’s Router for example, since merlin-wrt and many managed switches don’t easily support additional software.
Cloudflare Tunnels are Kind of similar to a VPN, only that you don’t connect your own devices with eachother, but instead connect your server(s) directly to cloudflare, who then take over the task of actually getting your data on the internet. The advantage of this is that you technically don’t even need a public IP address, since any requests and answers will be forwarded through the “VPN”, and only cloudflare needs to be publically accessible. This does require you to buy a Domain though, since that is what the forwarding will be based on. In the same vein, but if you want to do things “more manually”, I’d also recommend you look into Reverse proxying, if you haven’t already. That’s basically what turns “site1.example.com” and “site2.example.com” into different requests, usually to different IPs and/or Ports on your private network, allowing you to have multiple things running under one domain. Personally I use the “Nginx Proxy Manager” running in a Docker Container for this, mainly because it’s nice and easy to get your head around, but there are several newer Options like Traefik or Caddy that I also want to look into at some point.
After this wall of text, I hope you have fun playing around with all of this stuff, I know I had, and I really learned a lot about networks and the internet in general. Oh, and don’t be too stubborn to completely start from scratch occasionally, sometimes it’s just the easiest solution…
Thank you so much! This has been the most illustrative wall of text.
And you’re right, I might be a bit stubborn on wanting to learn things from scratch. I’ll be looking into Tailscale and Cloudflare tunnels. I was trying to mess around with wireguard, but I’m a bit lost and I don’t know how to configure iptables. I followed a video on youtube but so far managed to create a vpn within my local network (which I can’t access outside).
I’m also interested in nginx reverse proxy, but I don’t know where to start, I know I need docker, but I haven’t had a burning passion to learn docker yet (I may be a silly goose).
There are a lot of possibilities, but I’d like a starting point. Something that will teach me the most, but that won’t be holding my hand too much.
I really appreciate your comment, I shall keep thy wisdom for my future endeavors.
If you are looking for a vps to host your website, may I recommend Google cloud platform free tier? You have to give a credit card, and occasionally it messes up and charges $0.01 a month, but it’s pretty good.
Forward ports 80 and 443, set them up in nginx config and use certbot to get a SSL certificate if you have a domain for your site.
per your recommendation I just tried this, still the website is not loading and curl is not curling. If it helps, the error I get on my browser is “This site can’t be reached, my.public.ip.address took too long to respond”.
Haven’t done the certbot yet, I’m still trying to figure the port forwarding.
Are you running any firewall on your debian machine? Maybe install ufw firewall and open same ports in there. Then try again.
Don’t do that
Get a VPS and host it there.
Yeah I know, but why not? Care to give me a more detailed reason?
In short:
-
It is a major security risk. At the bare minimum you want to setup a reverse proxy and a certificate with Let’s encrypt
-
Your uptime is dependent on your Internet connection and hardware
Are you hosting a Static site? If so I would look into IPFS.
-
In my experience it’s not safe to port forward if you don’t know how everything works. Why don’t you use Tailscale? It works well and it even has Mulvad plugin
I’ve heard about this tailscale here and there, I’ll look into it, sounds promising. Thanks!
He’s serving a static html file, there isn’t much in the way of danger here that would be solved by Tailscale.
Now, I have a question.
If I port forward and someone gets into my kvm/qemu virtual machine, is there a way they could leave that environment and compromise the rest of my home network? The only port I’d be opening would be port 80, nothing more
Someone’s not really going to “get into” your virtual machine through a simple web server serving static files. Though it’s not impossible that you have some vulnerability with your web server software that allows for remote code execution on it, at which point its ability to do anything outside of that machine depends on a lot of things. If you’re exposing things to the public but don’t like the idea of the public interacting with machines on your home network, your best bet is to just host this on a VPS itself.
It’s probably a bit dangerous to expose your internal network in this way. If you really want a server running at home, there are interesting services which provide that for a fee, or you could set up a “reverse ssh proxy”.
It’s easier to do on some flavor of Linux, but you will set up a background service to ssh to a cloud server you rent, which links a local port on the cloud server to a local port on your home computer. You can then run a web service like caddy server on the cloud server to securely serve this port.
I realize this sounds rather complex, but something to look into and learn.
Your Caddyfile on the cloud server will look something like this:
my_subdomain.my_domain.com { reverse_proxy / { to 127.0.0.1:8081 } encode gzip }And the service on your local will look something like this:
[Unit] Description=Keeps a reverse tunnel to '<your cloud server ip>' open on port 8081 on the remote server After=network-online.target [Service] Environment="AUTOSSH_GATETIME=0" ExecStart=/usr/bin/autossh -N -M 10986 -o "PubKeyAuthentication=yes" -o "PasswordAuthentication=no" -o "ExitOnForwardFailure=yes" -R 8081:127.0.0.1:8080 root@<your cloud server ip> -i <path to your ssh key> -p 2097 ExecStop=/bin/kill $MAINPID Restart=always RestartSec=5 [Install] WantedBy=multi-user.targetYou will have to allow ssh on a non standard port (arbitrarily 2097 here), that way you can still use ssh on the standard port 22. I have some services running like this through a NAT for years.
This is nice to have, but it should be noted that doing it this way doesn’t mitigate much in the way of danger.
How does it not mitigate the danger? You are putting a secure web server in front of the tunnel rather than basically all traffic being forwarded to the port?
Well what “danger” are you talking about exactly? Traffic being forwarded to a port is not a danger. If the traffic being forwarded is going to a web server, proxying the exact same traffic through a different web server beforehand isn’t going to be any different.
Why don’t you use a Cloud flare zero trust tunnel? In this way you don’t need a public IP and open port on your router.
Cloudflare? Cloudflare acting as a MITM is the last thing I wish.
Cloudflare acting as a MITM
It is a MITM, but I think that for us self hoster ther’s nothing to worry about. What could they sniff? And it makes things easy.
deleted by creator





